Overview Of Jde Application Security 4t4819
This document was ed by and they confirmed that they have the permission to share it. If you are author or own the copyright of this book, please report to us by using this report form. Report 3b7i
Overview 3e4r5l
& View Overview Of Jde Application Security as PDF for free.
More details w3441
- Words: 1,004
- Pages: 3
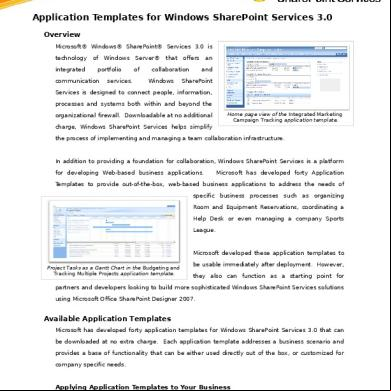
Overview of Application Security The information contained below is for use in conjunction with the Application Security Matrix Report (R5500951) from J. D. Edwards OneWorld.
Environment Access The purpose of each OneWorld environment is as follows: • • • • • • •
PD7333 – The live Production environment where most s access OneWorld. QA7333 – The Quality Assurance environment used for validation testing. PY7333 – The Prototype environment used for application testing and version creation. DV7333 – The Development environment used for creation and modification of objects. ES7333 – The ESU environment consists of Pristine OneWorld objects with PeopleSoft fixes applied. TR7333A – The Training environment used for end training. CV7333 – The Conversion environment used for testing data conversions.
Understanding OneWorld Security On specific objects, you can set the following levels of security, alone or in any combination, for s and groups: Group/: The identification code for a Profile or a Group. Three types of records may be displayed in this column. 1. – This security is set to a specific profile. (i.e. JDOE2) 2. GROUP –This security is set to a group of s with similar job requirements. DePuy security is set at the Group for all applications except Universal Table Browser. (i.e. DPY5710040) 3. *PUBLIC – This security is set as the default security assigned all s and groups. Group and security override *Public security on an application or report. Object Name: The OneWorld architecture is object based. The objects listed in this report are Batch Applications, Interactive Applications and Tables. When a ‘*ALL’ value is shown, the security applies to all objects.
Types of OneWorld Security: Column Security: Secures s from viewing a particular field or changing a value for a particular field. This can be a database or non-database field that is defined in the data dictionary, such as the work/calculated fields. For example, if you secure a from viewing the Salary field on the Employee Master application, the Salary field does not appear on the form when that accesses that application. Application Security - Three components:
Application Security: Secures s from running a particular application or a particular form within an application. Action Security: Secures s from executing a particular action, such as adding, deleting, revising, inquiring, or copying a record. Processing Option Security: Secures s from changing the values of processing options, or from prompting for versions and prompting for values for specific applications. When you secure a from prompting for versions, the will not be able to see the versions for a specific application. This means that from the current menu the will not be able to choose a different version of an application from the version that the assigned. Row Security: Secures s from accessing a particular range or list of records in any table. For example, if you secure a from accessing data about business units 1 through 10, the cannot view the records that pertain to those business units. Hyper Exit Security: Secures s from menu bar exits on OneWorld forms. These exits call applications and allow s to manipulate data. Exit security also restricts use of the hyper-button. External Calls Security: Secures s from accessing stand-alone executables that exist external to OneWorld. These external executables, which might include design tools, system monitors, and debugging tools, are specific to OneWorld. Tab Exit Security: Secures s from seeing a tab or tabs on a given form. Exclusive Application Security: Sets security specific to an application regardless of any other security that might be set. When you set exclusive application security for a , that gains access to just the specific application that you define. All other security still applies.
Other Used In The Report Data Item: Another name for the Alias (Such as AN8 for Address Book) and it refers to a unit of information such as a field. From Value: The From Data Value is used by the row security routines to determine a lower range for the data item in the specified table Thru Value: The Thru Data Value is used by the row security routines to determine an upper range for the data item in the specified table. View: This code designates whether a has the authority to view data either on a specific application or form (processing option and column security) or for a specific table and data item (row security).
Add: This code designates whether a has the authority to perform an add, either on a specific application or form (action and column security) or for a specific table and data item (row security). Change: This code designates whether a has the authority to perform changes, either on a specific application or form (action, processing option, and column security) or for a specific table and data item (row security). Delete: This code designates whether a has the authority to perform deletes, either on a specific application or form (action security) or for a specific table and data item (row security). OK/ Select: This code designates whether a has the authority to perform operations associated with the OK or Select button on a specific application or form (action security). Copy: This code designates whether a has the authority to perform operations associated with the Copy button on a specific application or form (action security). Scroll to End: This code designates whether a is given the option to scroll to the end of the data selected or if they will only be given the choice to view it a page at a time. Prompt for Versions: This code designates whether a will be allowed to prompt for the version of an application to run from a menu selection. Prompt for Values: This code designates whether a has the authority to ‘VIEW’ records in programs that are using Action Code Security. Run: This code designates whether a has the authority to run a specific application.
Environment Access The purpose of each OneWorld environment is as follows: • • • • • • •
PD7333 – The live Production environment where most s access OneWorld. QA7333 – The Quality Assurance environment used for validation testing. PY7333 – The Prototype environment used for application testing and version creation. DV7333 – The Development environment used for creation and modification of objects. ES7333 – The ESU environment consists of Pristine OneWorld objects with PeopleSoft fixes applied. TR7333A – The Training environment used for end training. CV7333 – The Conversion environment used for testing data conversions.
Understanding OneWorld Security On specific objects, you can set the following levels of security, alone or in any combination, for s and groups: Group/: The identification code for a Profile or a Group. Three types of records may be displayed in this column. 1. – This security is set to a specific profile. (i.e. JDOE2) 2. GROUP –This security is set to a group of s with similar job requirements. DePuy security is set at the Group for all applications except Universal Table Browser. (i.e. DPY5710040) 3. *PUBLIC – This security is set as the default security assigned all s and groups. Group and security override *Public security on an application or report. Object Name: The OneWorld architecture is object based. The objects listed in this report are Batch Applications, Interactive Applications and Tables. When a ‘*ALL’ value is shown, the security applies to all objects.
Types of OneWorld Security: Column Security: Secures s from viewing a particular field or changing a value for a particular field. This can be a database or non-database field that is defined in the data dictionary, such as the work/calculated fields. For example, if you secure a from viewing the Salary field on the Employee Master application, the Salary field does not appear on the form when that accesses that application. Application Security - Three components:
Application Security: Secures s from running a particular application or a particular form within an application. Action Security: Secures s from executing a particular action, such as adding, deleting, revising, inquiring, or copying a record. Processing Option Security: Secures s from changing the values of processing options, or from prompting for versions and prompting for values for specific applications. When you secure a from prompting for versions, the will not be able to see the versions for a specific application. This means that from the current menu the will not be able to choose a different version of an application from the version that the assigned. Row Security: Secures s from accessing a particular range or list of records in any table. For example, if you secure a from accessing data about business units 1 through 10, the cannot view the records that pertain to those business units. Hyper Exit Security: Secures s from menu bar exits on OneWorld forms. These exits call applications and allow s to manipulate data. Exit security also restricts use of the hyper-button. External Calls Security: Secures s from accessing stand-alone executables that exist external to OneWorld. These external executables, which might include design tools, system monitors, and debugging tools, are specific to OneWorld. Tab Exit Security: Secures s from seeing a tab or tabs on a given form. Exclusive Application Security: Sets security specific to an application regardless of any other security that might be set. When you set exclusive application security for a , that gains access to just the specific application that you define. All other security still applies.
Other Used In The Report Data Item: Another name for the Alias (Such as AN8 for Address Book) and it refers to a unit of information such as a field. From Value: The From Data Value is used by the row security routines to determine a lower range for the data item in the specified table Thru Value: The Thru Data Value is used by the row security routines to determine an upper range for the data item in the specified table. View: This code designates whether a has the authority to view data either on a specific application or form (processing option and column security) or for a specific table and data item (row security).
Add: This code designates whether a has the authority to perform an add, either on a specific application or form (action and column security) or for a specific table and data item (row security). Change: This code designates whether a has the authority to perform changes, either on a specific application or form (action, processing option, and column security) or for a specific table and data item (row security). Delete: This code designates whether a has the authority to perform deletes, either on a specific application or form (action security) or for a specific table and data item (row security). OK/ Select: This code designates whether a has the authority to perform operations associated with the OK or Select button on a specific application or form (action security). Copy: This code designates whether a has the authority to perform operations associated with the Copy button on a specific application or form (action security). Scroll to End: This code designates whether a is given the option to scroll to the end of the data selected or if they will only be given the choice to view it a page at a time. Prompt for Versions: This code designates whether a will be allowed to prompt for the version of an application to run from a menu selection. Prompt for Values: This code designates whether a has the authority to ‘VIEW’ records in programs that are using Action Code Security. Run: This code designates whether a has the authority to run a specific application.